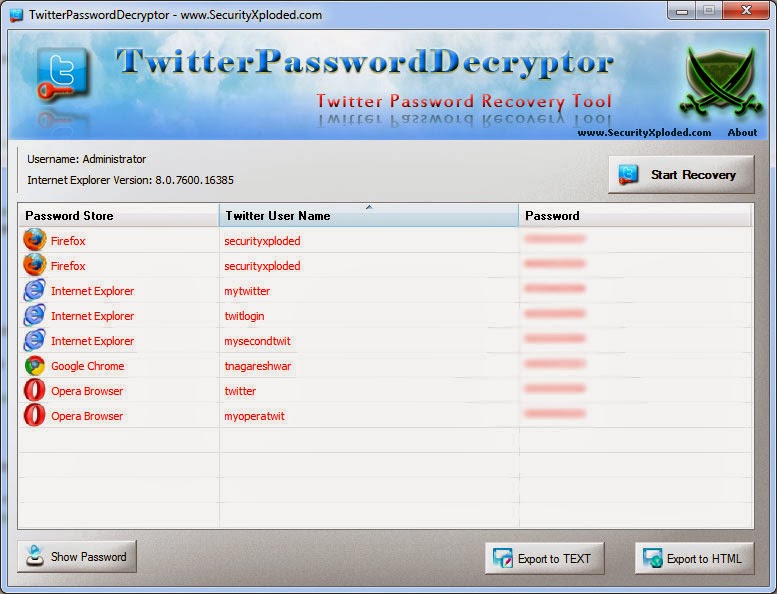
Twiter Account Password Cracker
After hacking into a social network account, the Hackers may try to take further advantage by sending messages to the real account holder. Their intentions could be malicious, such as to try to hack into their accounts. [27] Or the messages could be intended as a way to abuse the real account owner or a way to spread false or misleading information.
The origin of the Hackers, and their motives in hacking into the accounts, are not known. The accounts that the Hackers seized control of could be used by the Hackers to create deceptive messages to the accounts and their followers, to mislead potential victims, or, when the accounts are deleted, the accounts could be used to create new accounts.
It may take the Hackers time to steal data from accounts. For example, a hacker may wait until the current owner of a social media account has left his or her position at the company before stealing information. The Hackers may also download the web sites that are associated with the account, such as a company’s website or a business’s website, and then use this information to gain more information about the account holder or the company. The Hackers may search for and then copy the login credentials that will be needed to log in to the account. This may include the username and password, phone number, or email address that will be needed to log in to the account. When the Hackers have taken over an account, they may have access to the history of Tweets posted and replies sent by the account holder.
Usually, when hackers steal social media logins, they do so by impersonating people on social media and gaining access to the persons accounts. Although the Hackers stole the Twitter accounts and profiles of several celebrities and public figures, they did not steal the email addresses from those accounts. Unlike a normal phishing attack, where a hacker creates an email to impersonate someone and requests login information or a password, this Hackers used publicly available information about the accounts to redirect Twitter users to a scam website. [28] While the Hackers’ publicly available information may have compromised the accounts, they did not have to gain access to the real account holders email addresses.
hackers are using twitter to steal money, so they will do what they can to steal your money. the most common way of doing this is with a click bot. the hacker finds an account with an easy-to-guess username and password combination and clicks the bot and clicks the twitter icon. he will then be asked to login, and by clicking on the sign-in button, the hacker will be able to gain access to the account and log in.
some hackers are using a different approach to taking over the accounts. they are taking over the accounts of real people and then posting comments from fake accounts. they then search for accounts that are having problems with their account, and click the “report this user” button, and the twitter account will be closed for that person. the hacker will then use the phone number, email address, or username of the account, and log into the account. they then change the password and the username. this is where they gain control of the account.
these are the most straightforward ways to protect your twitter account and reduce the chance of being hacked. the best way to avoid getting hacked is to use good passwords that are hard to guess. a combination of letters and numbers is best, but don’t use the same password for all of your accounts. if possible, avoid using your personal information as a password. if you do, make sure its easy to remember, and change it.
using these methods, as well as others, can decrease the chances that you will be hacked. of course, not all passwords will be cracked. the number of accounts that can be cracked is increasing, and the time it takes to do so is decreasing. don’t panic.
5ec8ef588b
https://buycoffeemugs.com/saras-super-spa-me-full-version-free-download-link/
https://linesdrawn.org/coming-soon/
https://firstlady-realestate.com/2022/11/22/macdrive-9-pro-keygen-rar-checked-verified/
http://www.todaynewshub.com/wp-content/uploads/2022/11/Byomkesh_2015_Full_Movie_Download_TOP.pdf
https://xn--80aagyardii6h.xn--p1ai/davinci-resolve-15-crack-new/
https://womss.com/jamon-jamon-1992-720p-brrip-850mb-mkvcage/
https://news.mtkenya.co.ke/advert/jasc-paint-shop-pro-8-10-extras-rar/
https://vesinhnhatrang.com/2022/11/21/inside-out-english-2-full-movie-english-subtitles-download-torrent-patched/
https://thehomeofheroes.org/sketch-app-53-1-crack-license-key-2019-download-__hot__/
https://romans12-2.org/mp3directcut-v2-25-mp3-new/
https://kmtu82.org/download-ufc-undisputed-3-pc-torrent-link/
https://valentinesdaygiftguide.net/2022/11/21/spectaculator-v7-0-1-1310-winall-incl-updated-keygen-and-patch-brd/
http://wanoengineeringsystems.com/?p=171582
http://shop.chatredanesh.ir/?p=145525
http://turismoaccesiblepr.org/?p=37222
https://sahabhaav.com/wp-content/uploads/2022/11/3d_Desktop_Vdock_Exodo_Theme_Rar_Download_Full_Versionzip.pdf
https://aglgamelab.com/wp-content/uploads/2022/11/Spatial_Manager_For_Autocad_Crack_Activationl.pdf
https://dorisclothing.com/tom-jerry-golden-collection-dvd-download-6-2-gb-work/
https://xtc-hair.com/redgate-sql-prompt-keygen-download-better/
http://jwbotanicals.com/frozenway-crack-hotfile-mediafire-zip-full-link/